10 Bank Account Takeover Fraud Types and How to Prevent Them
October 27, 2025
These aren’t the bank account takeover risks of the 1990s or even the 2010s.
In what feels like no time at all, we’ve seen bank fraud risk change from “more of the same” to a totally new threat landscape thanks to bank fraudsters weaponizing AI faster than fraud teams have been able to respond.
In the last year, we saw just one AI-generated deepfake campaign steal nearly $4 million, and a staggering 92% of financial institutions report observing criminal use of Generative AI. Meanwhile, humans are as vulnerable as ever.
Even supposedly digital native Gen Z banking users are falling victim to scams at rates the same or even greater than their predecessors.
This means that in 2025, fraud rates are scaling rapidly at a level that will not be possible to prevent with status quo fraud detection solutions. Responding to alerts and flagging suspicious logins will no longer suffice. Banks need proactive, layered defense strategies that can adapt to evolving ATO tactics.
IronVest helps financial institutions detect and prevent account takeover attempts before damage is done, without compromising customer experience. Learn more.
To give you a pulse check on the 2025 ATO landscape, we’ve broken down ten major types of account takeover fraud, complete with real-world examples.
For each ATO type, we explain how it works, what makes it effective, and why banks need to pay closer attention.
What Is Bank Account Takeover Fraud?
Account takeover fraud (ATO) occurs when criminals hijack existing customer accounts (often by using stolen credentials or tactics like SIM swapping) to steal money or change account settings.
One Toronto-based content creator shared a striking ATO example earlier this year.
The scammer spoofed her bank’s phone number, claimed there were suspicious charges on her checking account, and even read out her real recent transactions to gain her trust.
During the call, he convinced her to provide her multi-factor authentication code, giving him full access to her accounts. He emptied her checking and savings accounts, maxed out her credit card, and locked her out of online banking.
The content creator said she asked for his full name, employee ID, and branch, but the scammer remained calm and professional throughout, making the fraud hard to spot. The police later confirmed they see these kinds of scams happen multiple times a day.
Account takeover fraud is not limited to the example above. We’ve catalogued ten distinct types of account takeover fraud that banks and their customers need to be aware of.
10 Bank Account Takeover Fraud Examples Your Financial Institution Needs to Know In 2025
Below, we share ten bank account takeover fraud examples to help you see what ATO looks like in 2025.
1. Credential reuse
One of the most common methods fraudsters use to initiate account takeovers is by attempting to use stolen credentials from other breaches on banking portals. If customers reuse usernames and passwords across sites, attackers can easily gain access.
A notable example is the PayPal credential stuffing attack, where cybercriminals accessed around 35,000 accounts using previously leaked credentials. In 2025, PayPal was fined $2 million for the breach.
Stolen credentials are being sold at an incredible volume. 1.7 billion stolen credential records were shared in underground forums last year.

2. Social engineering
Social engineering is when scammers manipulate banking customers or bank support staff into handing over sensitive information or access.
For example, the scammer might pretend to be a delivery company that needs confirmation of an address or date of birth to collect answers to security questions.
Variants of social engineering include:
Email phishing. Fake login portals or “urgent” messages to trick the target into revealing their login details.
Spear phishing. Personalized messages to gain the target’s trust.
Smishing. Malicious text messages, usually with fake banking links.
Vishing. Phone calls from attackers pretending to be from a financial institution.
Quishing. Malicious QR codes in emails, texts, and even printed letters disguised as from official institutions. When scanned, the code directs the victim to a fake login portal that harvests credentials or OTPs.
AI-powered deepfake impersonation. Voice cloning and deepfake video calls impersonating customers or bank staff. Fraudsters may call a bank’s customer service line, sounding exactly like the legitimate customer, convincing staff to reset credentials.
Attackers often pair social engineering with credential reuse or SIM hijacking to fully compromise accounts.
3. SIM hijacking
Once fraudsters have login details, they often need to bypass SMS-based 2FA. That’s where SIM swapping comes in.
By tricking or bribing telecom providers, attackers transfer a victim’s phone number to a SIM they control. This allows them to intercept SMS-based two-factor authentication (2FA) and reset access to bank accounts or apps.
A Bank of America customer lost $38,000 in a SIM-swapping attack after a fraudster hijacked his phone number, bypassed weak verification at his mobile provider, and used it to make multiple unauthorized wire transfers while he was asleep.
The FBI received 982 complaints about SIM swap attacks in 2024, many involving six-figure cryptocurrency losses or unauthorized bank transfers.
SIM cloning (where a fraudster makes a copy of a banking customer’s SIM card) exists, too, but swapping is far more common in real-world attacks.
4. MFA fatigue attacks
If an attacker spams a banking customer with hundreds of MFA requests, the customer may eventually approve one just to stop the constant notifications.
This is known as “MFA fatigue attack” or “push bombing.”

In this scenario, the attacker usually gets the customer’s login details through another vector (like a phishing attack or a data breach) and then tries to log into the customer’s account. The customer gets a notification asking them if they are trying to log in, and, because they are not, they deny it.
But the attacker doesn’t stop. They keep sending login attempts (sometimes late at night) until eventually, the customer gets frustrated or thinks it’s a glitch and grants them access.
The attacker is now logged into the customer’s account. They transfer money from the customer’s account to their own before the customer realizes what happened.
5. Account recovery exploitation
Account recovery exploitation is when a fraudster tricks the bank’s “forgot password” or account recovery process to take over your account.
An example of this attack is the attacker going to the customer’s bank’s “Forgot password?” page and entering the customer’s details, like their username, email, or phone number.
Banks that don’t enforce strong identity checks may reset customer passwords after the fraudster answers a few easy questions, such as “What’s your mother’s maiden name?” Most people’s mothers’ maiden names can be found via marriage and birth records.
The attacker then sets a new password, logs in, and empties the customer’s account. The customer only realizes what happened after they can no longer log in.
In some cases, fraudsters may call customer service and, pretending to be the customer, answer these questions over a phone call (combining social engineering with account recovery exploitation).
6. OAuth token theft
OAuth is a system that allows banking customers to log in or grant apps permission without sharing their passwords.

For example, a budgeting app might ask a user to "connect your bank account" to read their transactions. Instead of handing over their banking password, the customer authorizes access using an OAuth token, a special key with limited permissions.
OAuth token theft happens when fraudsters steal or trick users into handing over their OAuth token. They might use phishing sites disguised as legitimate apps, install malware on a user’s device, or intercept the token through a man-in-the-middle attack.
With a stolen token, a fraudster can do anything the token allows, such as downloading transaction history or even initiating payments. Even so-called “read-only” access can expose sensitive financial data that criminals can exploit.
OAuth tokens often remain active until the user manually revokes them, meaning token theft can go undetected for long periods, especially since the account still appears fully functional to the customer.
7. Keylogging/malware-based takeover
Some attackers install keyloggers on a customer’s device via phishing emails or fake software updates.
The malware runs in the background, recording the customer’s keystrokes and taking screenshots when they’re on your banking app or site. The attacker can then take over the customer’s banking account with this stolen information.
In one case involving a small family-owned business that used online banking and automated clearing house (ACH) transfers extensively, fraudsters installed malware containing keyloggers that recorded employee keystrokes and captured banking credentials. This enabled the fraudsters to make multiple unauthorized ACH transfers totaling around $550,000 in just one week.
8. Session hijacking
When a customer logs in, banks issue a session token to authenticate future activity.
In session hijacking, malware on the victim’s device intercepts that token and sends it to the attacker, who then uses it to impersonate the customer, bypassing logins and MFA.
And since the requests come with a valid session token, the bank’s systems believe the actions are being performed by the legitimate user, which makes detection much more difficult.
Unlike Man-in-the-Browser attacks (discussed below), which alter what a customer sees and submits, session hijacking focuses on stealing the authentication token itself.
9. Man-in-the-Browser attacks
A more advanced malware technique, Man-in-the-Browser (MitB) attacks, involves a criminal installing malware (for example, through a phishing email) inside a banking customer’s web browser.
The malware can silently alter payment details in real time, so while the customer thinks they’re sending money to “Landlord,” it’s actually going to the attacker.
The customer doesn’t notice anything is wrong because the browser shows fake details.
This type of attack works even with HTTPS encryption because the attack happens inside the browser, after the encryption.
Multi-factor authentication doesn’t work here, either. When a customer types in the code, the malware forwards it to the attacker. Meanwhile, the customer still sees a fake “successful transaction” screen.
10. Cross-channel fraud
The most advanced ATO attacks combine multiple methods into coordinated, multi-step campaigns.
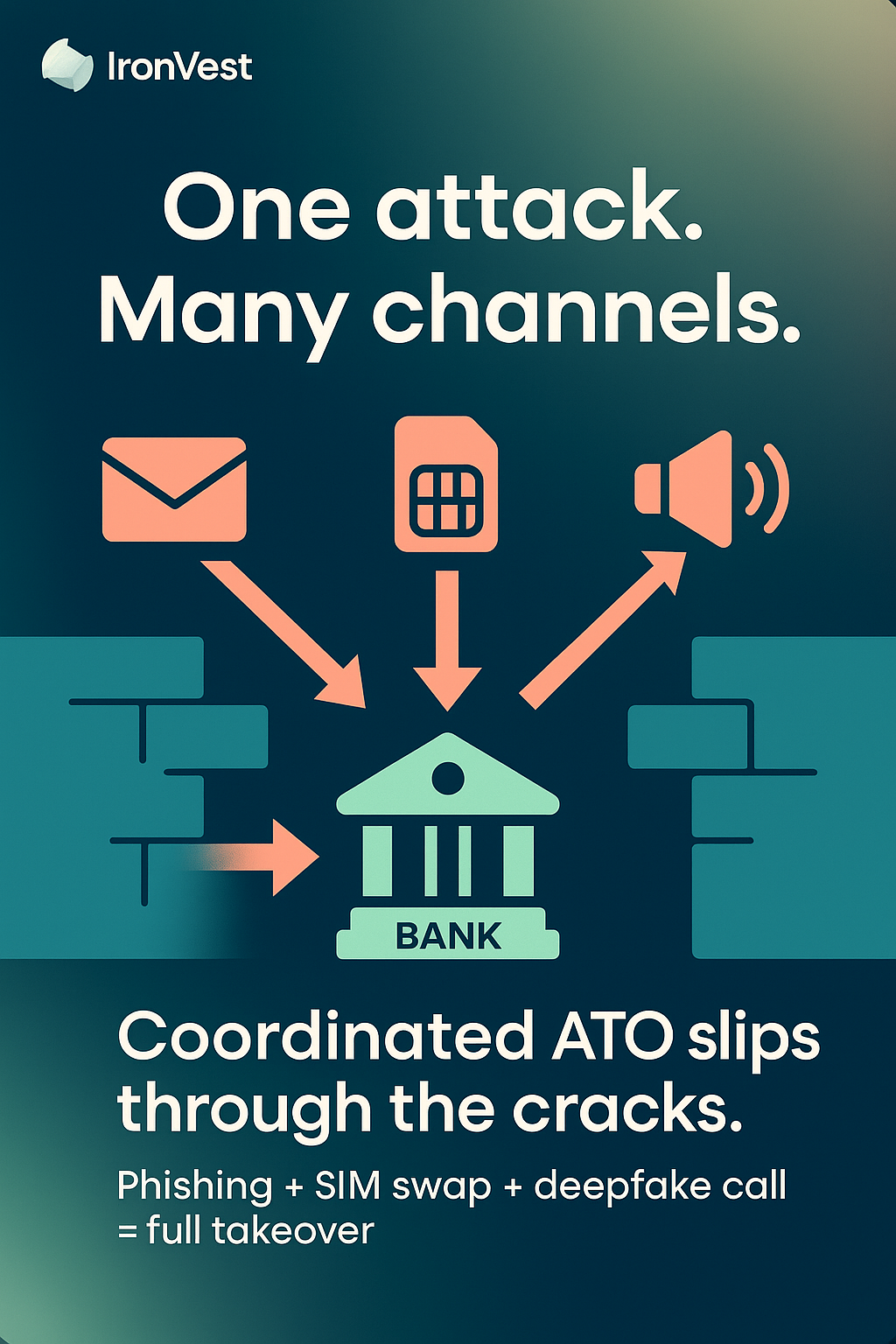
A typical example might involve:
Phishing for credentials.
SIM swapping to intercept 2FA codes.
Deepfake voice calls to the bank’s customer service to reset the customer’s password.
By targeting multiple channels, scammers exploit the gaps between bank defenses.
2025 Bank Account Takeover Fraud Statistics
To help illustrate the scale and scope of the account takeover (ATO) threat in 2025, we’ve compiled some of the most recent and relevant statistics, all published this year.
Financial services remain the top target for account takeover attacks, making up 22% of all reported incidents. (Source)
ATO fraud accounted for 27% of all fraud cases globally in 2024, a slight year-over-year decrease of about 2%. (Source)
In 2024 alone, security systems detected over 3 billion brute-force ATO attempts, highlighting the scale of automated attack methods. (Source)
Bank Account Takeover Fraud Prevention with Unhackable Authentication
IronVest helps banks defend against account takeover fraud by continuously linking identity to every user action, not just at login.
With IronVest ActionID, identity verification becomes a continuous, in-session process. Instead of checking who the user is just before a transaction, we verify identity before, during, and after every action.
IronVest’s ActionID makes it impossible for attackers to hijack accounts, protecting your financial institution from costly ATO losses and safeguarding your customers from identity theft and credential abuse.
Get a demo of IronVest today to discover how you can stop account takeover scams at scale.